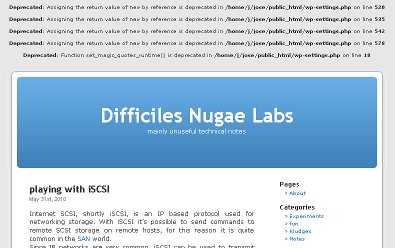
If, due to your provider php configuration, Your wordpress pages are writing some error messages like
Deprecated: Assigning the return value of new by reference is deprecated in /home/j/jose/public_html/wp-settings.php on line 520
Deprecated: Assigning the return value of new by reference is deprecated in /home/j/jose/public_html/wp-settings.php on line 535
Deprecated: Assigning the return value of new by reference is deprecated in /home/j/jose/public_html/wp-settings.php on line 542
Deprecated: Assigning the return value of new by reference is deprecated in /home/j/jose/public_html/wp-settings.php on line 578
Deprecated: Function set_magic_quotes_runtime() is deprecated in /home/j/jose/public_html/wp-settings.php on line 18
In lost-in-code website You can find the solution: just add theese two lines
error_reporting(0);
@ini_set(‘display_errors’, 0);
at the bebinning og wp-config.php file.